Understanding The Essentials Of "Log In Or Sign Up": A Comprehensive Guide
In today's digital age, the terms "log in" and "sign up" have become an integral part of our online experiences. Whether you're accessing your email, social media platforms, or any other online service, these terms are your gateways. They are the keys that unlock the digital world for you, enabling you to engage, interact, and perform numerous activities. Despite their ubiquity, many users still find themselves confused about the difference between the two and the significance they hold in the realm of cybersecurity.
The process of logging in and signing up is more than just entering a username and password. It is about establishing your identity in the digital landscape. This identity allows you to personalize your experience, access exclusive features, and ensure your data is secure. Understanding the nuances between logging in and signing up can greatly enhance your online security and improve your interaction with various platforms.
This comprehensive guide aims to demystify the concepts of "log in" and "sign up". We'll explore the differences, the importance of secure credentials, and how these processes have evolved over time. Additionally, we'll delve into the best practices to enhance your cybersecurity and troubleshoot common issues that might arise. Whether you're a digital newcomer or a seasoned internet user, this guide is designed to provide you with a thorough understanding of these essential digital processes.
Table of Contents
- Biography of the Log In and Sign Up Process
- Understanding "Log In" and "Sign Up"
- Importance of Secure Credentials
- Evolution of the Login and Sign-Up Process
- Security Measures in Login and Sign-Up
- Best Practices for Secure Login and Sign-Up
- Troubleshooting Common Issues
- Enhancing User Experience in Login and Sign-Up
- The Role of Multi-Factor Authentication
- Privacy Concerns and Data Protection
- The Future of Login and Sign-Up Processes
- Frequently Asked Questions
- Conclusion
Biography of the Log In and Sign Up Process
The concepts of "log in" and "sign up" have evolved significantly since the dawn of the internet. Initially, these processes were rudimentary and primarily used by institutions and organizations to secure sensitive data. Over time, as the internet became more accessible, the demand for user-friendly authentication processes grew.
The "log in" process involves accessing an existing account using a username and password. This method ensures that only authorized individuals can access the account. On the other hand, "sign up" refers to the creation of a new account. During this process, users provide personal information which is stored by the service provider for future authentication.
Personal Details and Biodata
| Login | Sign Up |
|---|---|
| Access existing account | Create new account |
| Requires username and password | Requires personal information |
| Used for authentication | Used for account creation |
Over the years, the processes have incorporated advanced security measures like encryption, two-factor authentication, and biometric verification. As we continue through this guide, we will explore these developments in detail and understand their impact on user security and experience.
Understanding "Log In" and "Sign Up"
To navigate the digital landscape effectively, it is crucial to understand the differences between "log in" and "sign up". Although they are often used interchangeably, they serve distinct purposes and are integral to maintaining your digital identity.
Log In
"Log in" refers to the action of entering credentials to access an existing account. It is akin to unlocking a door with a key – the username and password being the key. This process verifies that you have the right to access the account and its data. Logging in is a frequent activity for users who need to access services like email, banking, or social media.
Common Login Methods
- Username and Password
- Social Media Login
- Single Sign-On (SSO)
- Biometric Login (Fingerprint, Facial Recognition)
Each login method has its advantages and challenges. For instance, social media login offers convenience but may raise privacy concerns. Understanding these methods helps users choose the one that aligns with their security needs and preferences.
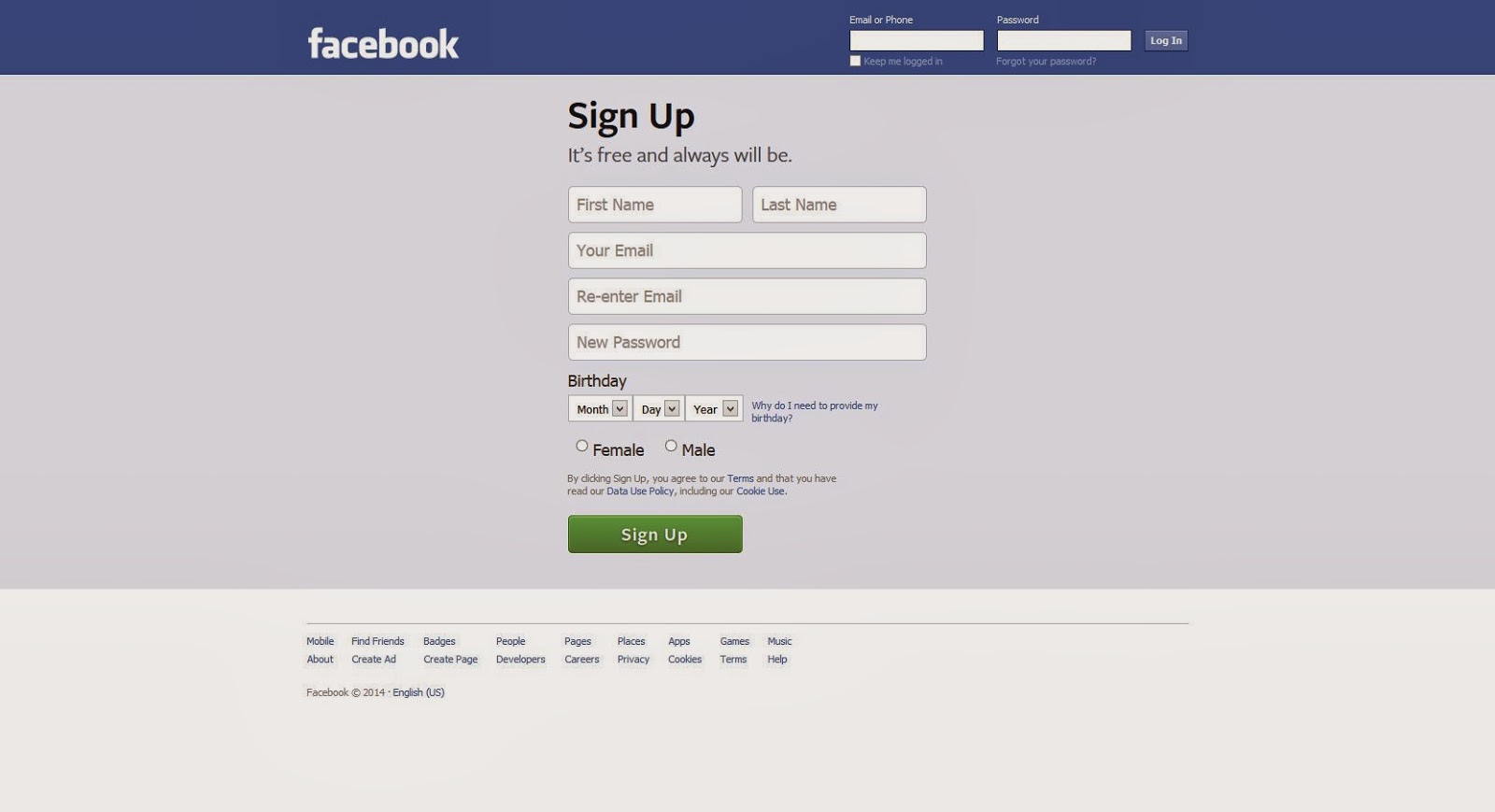
Sign Up
"Sign up" is the process of creating a new account on a platform. This involves providing personal details and setting up a username and password. When you sign up, you're essentially creating a new digital identity for that platform or service. This process often requires additional verification like email or phone number confirmation to ensure the authenticity of the user.
Steps in the Sign-Up Process
- Provide Personal Information
- Create a Username and Password
- Verify Email or Phone Number
- Agree to Terms and Conditions
- Complete CAPTCHA Verification
Understanding the intricacies of the sign-up process allows users to provide accurate information and make informed decisions regarding the services they wish to use.
Importance of Secure Credentials
Secure credentials are the cornerstone of a safe online experience. They protect your personal information, prevent unauthorized access, and maintain the integrity of your digital identity. Weak or compromised credentials can lead to data breaches, identity theft, and other cyber threats.
Creating Strong Passwords
One of the most effective ways to secure your credentials is by creating strong passwords. A strong password is typically a combination of letters, numbers, and special characters. It should be unique and not easily guessable.
Password Creation Tips
- Use a mix of uppercase and lowercase letters
- Include numbers and special characters
- Avoid using easily guessable information like birthdays or names
- Consider using a password manager to store and generate complex passwords
Creating strong passwords is just the first step. Users must also be diligent in updating their passwords regularly to mitigate the risk of unauthorized access.
Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring an additional verification step beyond the password. This could be a code sent to your mobile device or an authentication app. 2FA significantly reduces the likelihood of unauthorized access even if your password is compromised.
By incorporating 2FA, users can enhance their security and protect their digital identities from potential threats. As we delve deeper into this guide, we'll explore other security measures that can further fortify your login and sign-up processes.
Evolution of the Login and Sign-Up Process
The login and sign-up processes have come a long way since their inception. As technology has advanced, so too have the methods by which we authenticate our digital identities. This evolution reflects the growing importance of cybersecurity and the need for user-friendly authentication methods.
Early Days of Authentication
In the early days of the internet, login and sign-up processes were rudimentary. They relied heavily on simple username and password combinations. These methods were adequate for the time but lacked the sophistication needed to combat modern cyber threats.
Challenges of Early Authentication Methods
- Susceptibility to brute force attacks
- Lack of encryption
- Limited user verification methods
As cyber threats became more prevalent, the need for advanced security measures became apparent. This led to the development of more secure and efficient authentication processes.
Modern Authentication Techniques
Today, login and sign-up processes incorporate a variety of advanced techniques designed to improve security and user experience. These include biometric verification, single sign-on, and multi-factor authentication, among others. These techniques offer enhanced security while also providing users with convenient ways to access their accounts.
Benefits of Modern Authentication
- Improved Security
- Enhanced User Experience
- Greater Flexibility and Convenience
The evolution of login and sign-up processes is a testament to the continuous efforts to balance security and usability. As we move forward, it is crucial to stay informed about new authentication technologies and best practices.
Security Measures in Login and Sign-Up
Security measures play a vital role in safeguarding your digital identity during the login and sign-up processes. These measures are designed to protect your personal information and prevent unauthorized access to your accounts.
Encryption
Encryption is a process that converts your data into a coded format, making it unreadable to unauthorized users. It is an essential security measure in the login and sign-up processes, as it ensures that your credentials are protected during transmission.
Types of Encryption Used
- SSL/TLS Encryption
- End-to-End Encryption
- Hashing Algorithms (e.g., SHA-256)
By employing encryption, service providers can significantly reduce the risk of data breaches and protect user information from cyber threats.
CAPTCHA Verification
CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) is a security measure used to differentiate between human users and automated bots. It is commonly used in the sign-up process to prevent fraudulent account creation.
Types of CAPTCHA
- Text-Based CAPTCHA
- Image-Based CAPTCHA
- ReCAPTCHA
CAPTCHA verification is an effective tool for preventing automated attacks and ensuring that only genuine users can access a platform.
Best Practices for Secure Login and Sign-Up
Adopting best practices for secure login and sign-up can significantly enhance your online security and protect your digital identity. These practices involve creating strong credentials, using additional security measures, and staying informed about potential threats.
Regularly Update Passwords
One of the simplest yet most effective ways to secure your accounts is by regularly updating your passwords. This reduces the risk of unauthorized access and ensures that your credentials remain secure.
Password Update Tips
- Change passwords every 3-6 months
- Use a password manager to track and generate passwords
- Avoid reusing old passwords
By maintaining a routine of regular password updates, users can enhance their security and protect their accounts from potential threats.
Enable Two-Factor Authentication
Two-factor authentication adds an additional layer of security to your login process. By requiring a second verification step, such as a code sent to your mobile device, you can significantly reduce the risk of unauthorized access.
Benefits of Two-Factor Authentication
- Increased Account Security
- Protection Against Phishing Attacks
- Enhanced User Confidence
Enabling two-factor authentication is a crucial step in fortifying your online security and ensuring the protection of your digital identity.
Troubleshooting Common Issues
Despite the best efforts to secure login and sign-up processes, users may encounter various issues that can hinder their access to online services. Understanding common issues and their solutions can facilitate a smoother user experience.
Forgotten Passwords
One of the most common issues users face is forgetting their passwords. Fortunately, most platforms offer a password recovery option, which typically involves verifying your identity through an email or phone number.
Steps to Recover a Forgotten Password
- Click on "Forgot Password" on the login page
- Enter your registered email or phone number
- Follow the instructions in the recovery email or message
- Create a new password and confirm it
By following these steps, users can regain access to their accounts and continue using the services.
Account Lockouts
Account lockouts occur when multiple failed login attempts trigger a security mechanism, preventing further access. This is a protective measure against unauthorized access but can be frustrating for legitimate users.
Steps to Resolve Account Lockouts
- Wait for the lockout period to expire
- Follow the account recovery process
- Contact customer support for assistance
By understanding the causes of account lockouts and how to resolve them, users can minimize disruptions and maintain access to their accounts.
Enhancing User Experience in Login and Sign-Up
Enhancing the user experience in login and sign-up processes is essential for maintaining user satisfaction and engagement. A seamless experience not only improves user retention but also enhances the overall perception of the platform.
User-Friendly Interfaces
User-friendly interfaces make the login and sign-up processes intuitive and accessible. Simple, clean designs with clear instructions can enhance user experience and reduce frustration.
Elements of User-Friendly Interfaces
- Clear and Concise Instructions
- Responsive Design for Different Devices
- Accessible Options for All Users
By incorporating user-friendly elements, platforms can improve the accessibility and satisfaction of their users.
Personalization Options
Offering personalization options during the sign-up process can enhance user engagement and provide a more tailored experience. Users appreciate the ability to customize their profiles and settings according to their preferences.
Personalization Features
- Customizable Profile Settings
- Notification Preferences
- Theme and Layout Options
By providing personalization features, platforms can foster a sense of ownership and satisfaction among users, improving their overall experience.
The Role of Multi-Factor Authentication
Multi-factor authentication (MFA) is a critical component of modern security strategies, providing an additional layer of protection for login and sign-up processes. MFA requires users to verify their identity through two or more separate factors, making it more difficult for unauthorized access.
Types of Multi-Factor Authentication
MFA can involve a combination of different authentication factors, such as:
- Something You Know (Password or PIN)
- Something You Have (Smartphone, Security Token)
- Something You Are (Biometric Verification)
By incorporating multiple factors, MFA ensures that even if one factor is compromised, unauthorized access is still prevented.
Advantages of Multi-Factor Authentication
- Enhanced Security
- Protection Against Phishing and Social Engineering
- Increased User Trust and Confidence
Implementing MFA is a proactive measure to safeguard your digital identity and protect against emerging cyber threats.
Privacy Concerns and Data Protection
Privacy concerns are paramount in the digital age, where personal information is a valuable commodity. Ensuring data protection during login and sign-up processes is crucial for maintaining user trust and compliance with regulations.
Data Collection and Storage
During the sign-up process, platforms collect personal information such as names, email addresses, and phone numbers. It is essential to ensure that this data is collected and stored securely to prevent unauthorized access and misuse.
Data Protection Best Practices
- Implement Data Encryption
- Regularly Update Security Protocols
- Limit Data Collection to Essential Information
By adhering to these best practices, platforms can enhance data protection and mitigate privacy concerns.
Compliance with Regulations
Compliance with data protection regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), is essential for maintaining user trust and avoiding legal repercussions.
Key Compliance Requirements
- Obtain User Consent for Data Collection
- Provide Transparency on Data Usage
- Offer Options for Data Deletion and Access
By ensuring compliance with these regulations, platforms can build trust with their users and demonstrate their commitment to data protection.
The Future of Login and Sign-Up Processes
The future of login and sign-up processes is shaped by emerging technologies and evolving security needs. As cyber threats become more sophisticated, the need for innovative authentication methods continues to grow.
Biometric Authentication
Biometric authentication, which uses unique biological characteristics like fingerprints or facial recognition, is poised to play a significant role in future login and sign-up processes. It offers a convenient and secure way to authenticate users without the need for traditional passwords.
Advantages of Biometric Authentication
- Convenience and Ease of Use
- Increased Security and Accuracy
- Reduced Reliance on Passwords
As biometric technology advances, it is likely to become a standard component of authentication processes.
Decentralized Identity Solutions
Decentralized identity solutions, which give users control over their digital identities, are gaining traction as a way to enhance privacy and security. These solutions leverage blockchain technology to provide a secure and transparent way to manage digital identities.
Benefits of Decentralized Identity
- User Control Over Personal Data
- Reduced Risk of Data Breaches
- Enhanced Privacy and Security
Decentralized identity solutions represent a promising future for login and sign-up processes, offering users greater control and security over their digital identities.
Frequently Asked Questions
1. What is the difference between "log in" and "sign up"?
"Log in" refers to accessing an existing account using credentials, while "sign up" involves creating a new account with personal information.
2. Why is two-factor authentication important?
Two-factor authentication provides an additional layer of security, making it more difficult for unauthorized users to access your accounts.
3. How can I create a strong password?
Create a strong password by using a combination of letters, numbers, and special characters. Avoid using easily guessable information and consider using a password manager.
4. What should I do if I forget my password?
If you forget your password, use the password recovery option on the login page and follow the instructions to reset your password.
5. How can I improve my online security during login and sign-up?
Improve your online security by creating strong passwords, enabling two-factor authentication, and staying informed about potential threats.
6. What are the benefits of biometric authentication?
Biometric authentication offers convenience, increased security, and reduced reliance on traditional passwords by using unique biological characteristics for authentication.
Conclusion
In conclusion, the processes of "log in" and "sign up" are fundamental to our online experiences, serving as the gateways to our digital identities. Understanding their significance, security measures, and best practices is crucial for protecting our personal information and ensuring a safe online environment. As technology continues to evolve, it is essential to stay informed about emerging authentication methods and security measures. By adopting these practices, users can enhance their online security and enjoy a seamless digital experience.
For more information and insights on login and sign-up processes, consider visiting reputable cybersecurity websites or consulting with experts in the field.
Article Recommendations
- Charcoal Grill Chicken Wings
- Lumberjack Halloween Outfit
- Elavil And Alcohol
- Rosemarie Fritzl
- Harvard Egg And Feed
- Matt Dillon Wife
- Ephesians 5 22 25
- Bobby Charlton
- Bread And Fred
- Weather Biloxi Ms